How to Configure K3s with Traefik Ingress Controller Example
Posted March 20, 2024
This guide teaches how to perfectly set up and Configure a K3s Kubernetes cluster with the Traefik Ingress Controller example. K3s is a tightly packaged Kubernetes distribution. It comes with all Kubernetes cluster batteries included. This means K3s gives you all Kubernetes core components to create a lightweight Kubernetes cluster.
In this comprehensive guide, you will explore Traefik v2 as K3s Ingress Controller. You will learn all Traefik K3s components and how to use them in your cluster. Ready? Dive into this tutorial Configure K3s with the Traefik Ingress Controller example.
Introducing Traefik as k3s Ingress Controller
Once you install K3s, you get Traefik to expose a service to the web. Traefik is wide. It, at the same time creates K3s HTTPS with Let’s Encrypt and K3s Dashboards. A traditional Kubernetes cluster uses Ingress Controllers to define how you access K8s cluster resources externally.
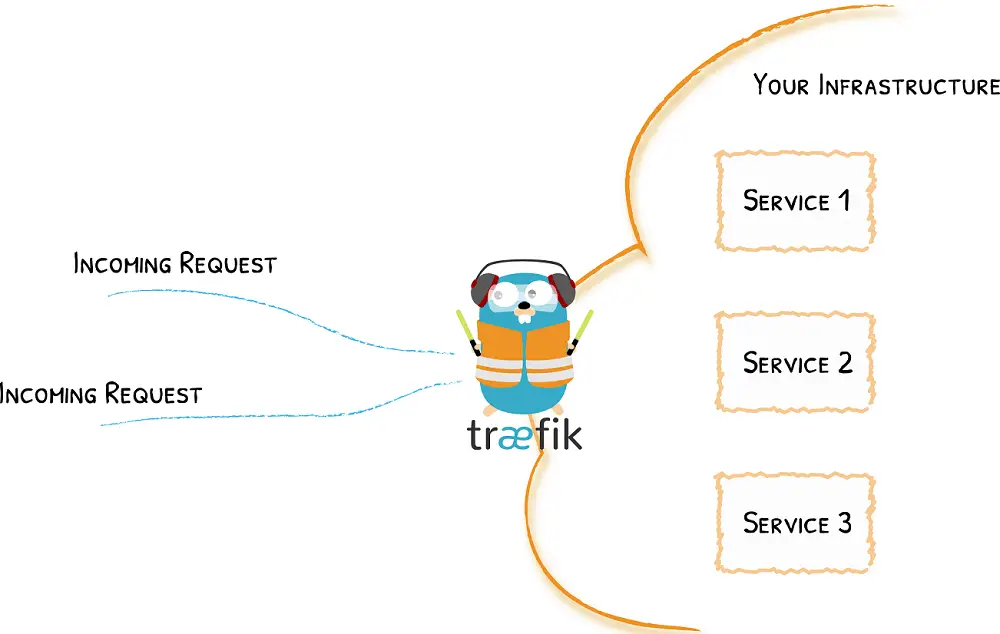
K3s uses Traefik v2 with Ingress Route as the Controller example. You now understand that Ingress Traefik acts as an Ingress Controller. The good thing with K3s is that Traefik picks up your Ingress objects and configures itself accordingly.
The default K3s settings will deploy Traefik as an Ingress Controller and you don’t have to set it up from scratch. From there, you will create your deployments and use Ingress Controller for networking exposing your services, and proxying the traffic correctly.
Installing k3s with Traefik Ingress Controller
Traefik is your modern Ingress HTTP reverse proxy and load balance. It acts as your Network Policy Controller. Now get Ingress Traefik Configure ready K3s must be installed and running:
Use the following command to get K3s ready:
curl -sfL https://get.k3s.io | sh -
Or check these guides to get started:
- Install K3s on Ubuntu 20.04|22.04 Step-by-Step
- Mastering K3s on macOS – Install and Provision K3s with K3D on macOS
K3s should be ready and running.
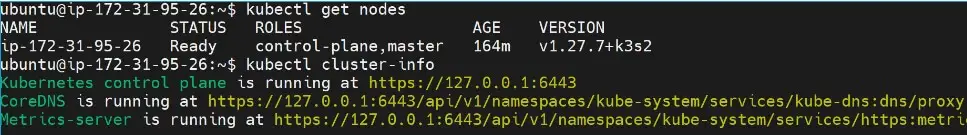
Examining Installed K3s Traefik Ingress Controller
The Installed Ingress is added by default. Now, if you check all pods running in your kube-system, you will have all k3s Traefik pods running as such:
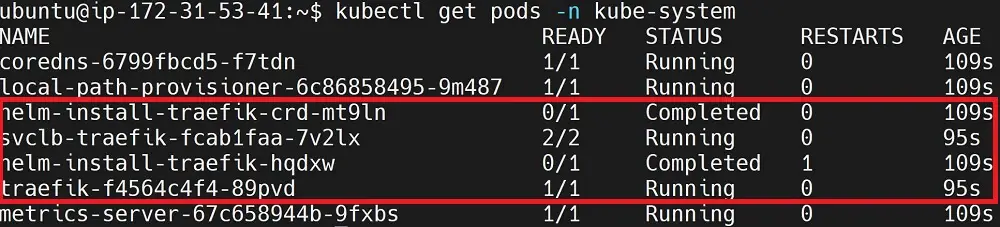
Traefik Ingress Controller will manage all these components in a traefik.yaml file located in /var/lib/rancher/k3s/server/manifests
Now, cd to cd /var/lib/rancher/k3s/server/manifests:
You might need to first run
sudo su -to elevate directory permissions
cd /var/lib/rancher/k3s/server/manifests
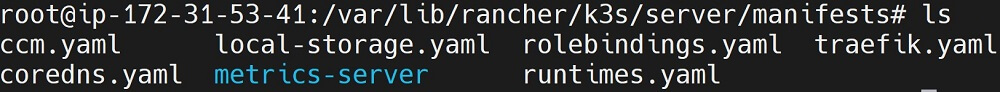
You can open this file and check its content as such:
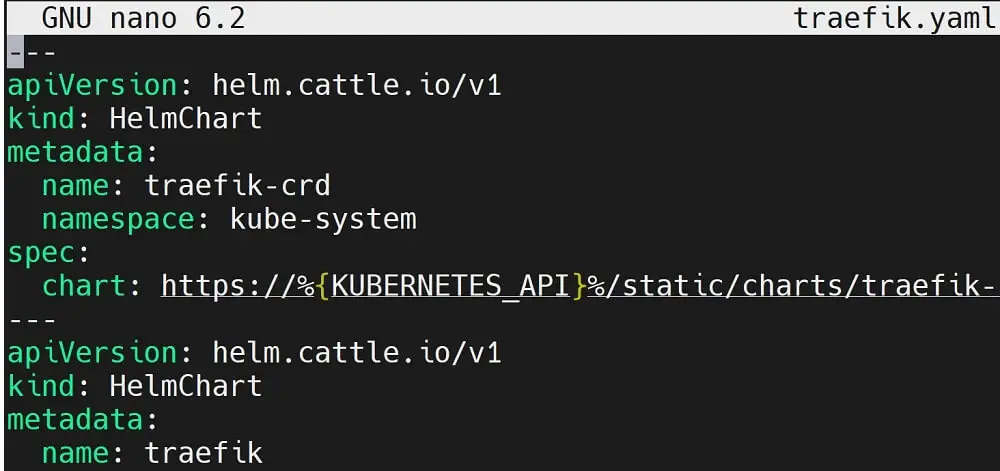
However, this file is the default. DO NOT edit it manually.
You can now see the Traefik is ready and uses HelmChartConfig manifest. Let’s now create K3s clusters and use Traefik Ingress Controller to expose them.
How K3s Traefik Ingress Controller Works
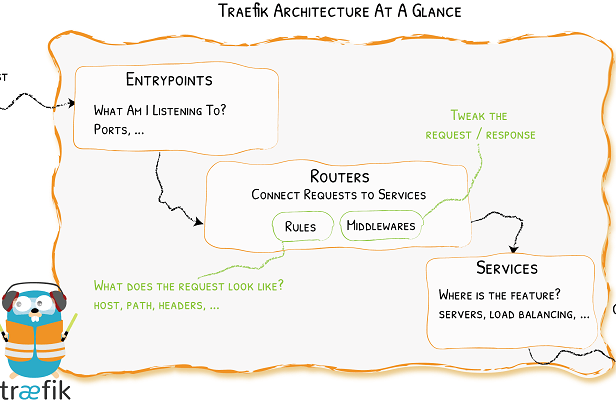
For K3s to handle the Ingress Controller and expose your cluster, Traefik will need:
- EntryPoints as the application port numbers.
- Router to connect incoming requests to the application service
- Service to tell Traefik how to reach to the actual application service the Ingress Controller will handle the incoming requests.
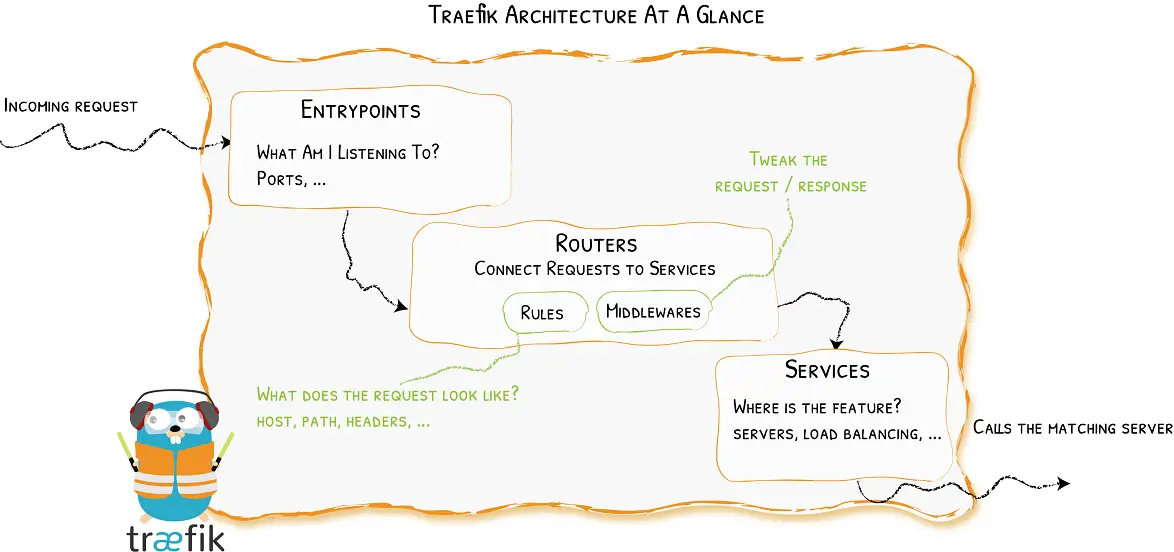
By default, K3s will use 80 and 443 as Traefik ingress controller host ports. This means the Traefik ingress controller deploys a Load Balancer Service and directs traffic to these ports.
Host ports 80 and 443 are the standard ports that let Traefik create HTTP and HTTPS ingresses for Load Balancers and proxying traffic.
A K3s Node Pools will use the ServiceLB and expose these ports on all cluster members. These ports will not be usable for other HostPort or NodePort pods.
ServiceLB will watch any spec.type set to LoadBalancer and forward traffic from the Pod’s NodePort to the Service’s ClusterIP address and port (80 or 443).
Traefik will modify the current traefik.yaml chart will different values. A good example of such changes is created in this value.yaml file.
You might consider checking this guide and learning how Traefik handles Load Balancing.
Exposing Service using Traefik Ingress Controller Example
Now, with the above newfound knowledge, let’s use Traefik to create an Ingress Controller within an app running on K3s.
Keep in mind, K3s Ingress will only work with default ports 80 and 443. Therefore, in this first example, you will use K3s and Traefik Ingress to only route and load balance an application that runs on either port 80 or 443.
To make it simple, I will only use either Apache or NGINX, as they run on port 80 by default.
In your working directory create a deployment.yml file and run an Apache HTTP Server with K3s as follows:
# Apache HTTP Server Deployment
apiVersion: apps/v1
kind: Deployment
metadata:
name: apache-deployment
spec:
replicas: 3
selector:
matchLabels:
app: apache
template:
metadata:
labels:
app: apache
spec:
containers:
- name: apache
image: httpd:latest
ports:
# Container port where Apache listens
- containerPort: 80
# Apache HTTP Server Service
---
apiVersion: v1
kind: Service
metadata:
labels:
app: apache
name: apache-service
spec:
ports:
- name: http
port: 80
protocol: TCP
# Expose port 80 on the service
targetPort: 80
selector:
# Link this service to pods with the label app=apache
app: apache
# Apache HTTP Server Ingress
---
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: apache-ingress
spec:
rules:
- http:
paths:
- path: /
pathType: Prefix
# Redirect traffic to service on port 80
backend:
service:
name: apache-service
port:
number: 80
Because your main interest is in using the Ingress Controller, we will concentrate on the following part:
# Apache HTTP Server Ingress
---
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: apache-ingress
spec:
rules:
- http:
paths:
- path: /
pathType: Prefix
# Redirect traffic to service on port 80
backend:
service:
name: apache-service
port:
number: 80
Here:
- K3s will create your deployment.
- Add a service that exposes port 80 on your pod.
- Create an Ingress resource to point to the Apache service
This means the Traefik Ingress controller will use:
- EntryPoint as port 80 where Ingress will listen to the incoming requests.
- Run Service
apache-servicewhere the actual application is running to the Ingress Controller. - Router is denoted with
pathsas the path (/) where Traefik Ingress Controller will redirect traffic to service on port 80.
Digesting a K3s Traefik Ingress Controller Resource
To understand how this works, let’s deploy the above resource. Use the following command in your deployment.yml file location:
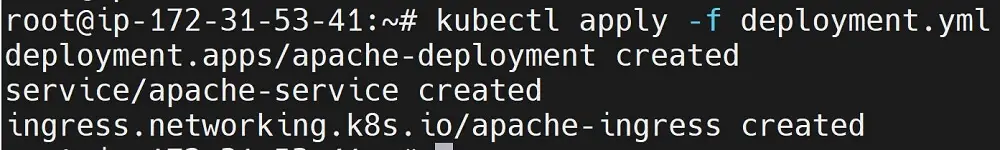
To get more details about Ingress, run the following command:
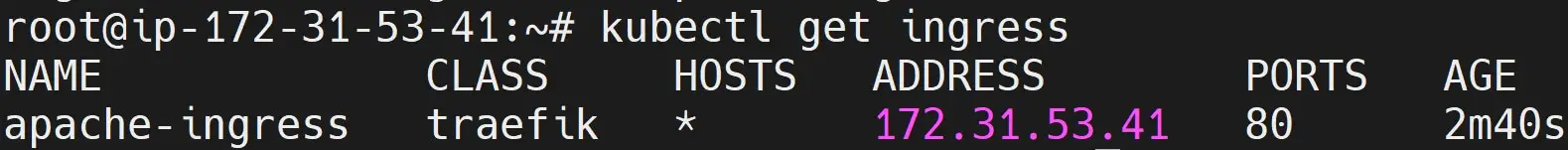
kubectl get ingress
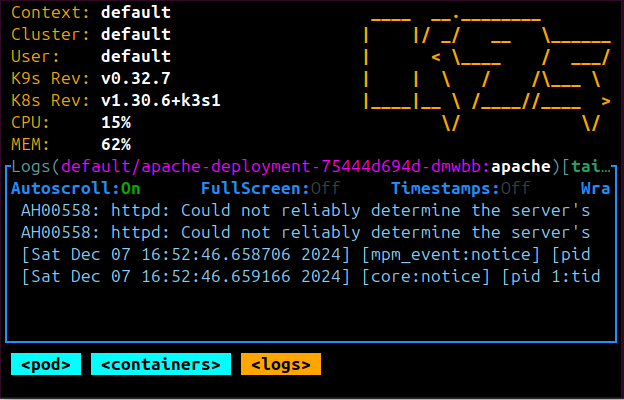
Now, K3s will show you the ingress names, hosts, and paths. In this case, the Apache should be running on port 80 and using Traefik as the Ingress Controller:
To get even more details, describe the Ingress resource using this command:
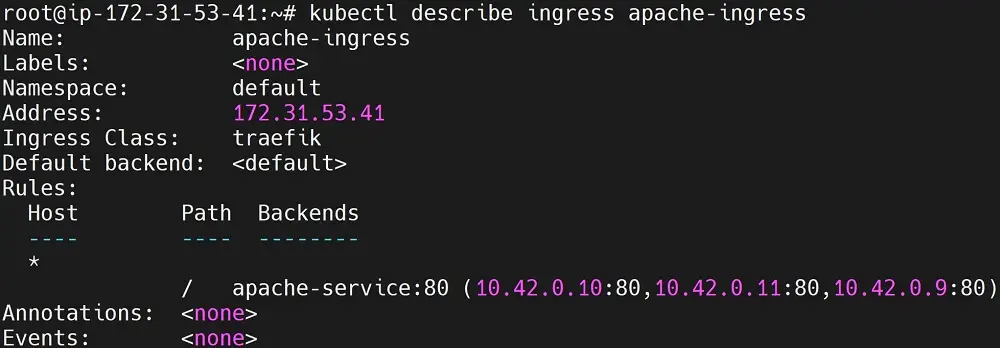
kubectl describe ingress apache-ingress
You will have all the namespace, annotations, and rules for this ingress class as such:
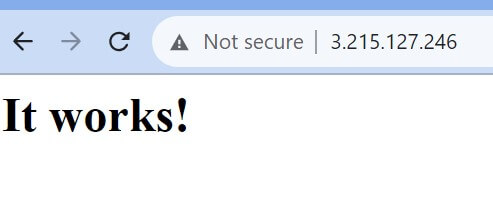
At this time Ingress Controller will use Traefik to expose Apache. This way, you will access the app using: http://Your_IP_Address>:80
At the same time, if you are running the same application on a remote server, the application will be exposed to the home path (/) as http://Your_IP_Address>:
K3s with Traefik Dashboards and Traefik HTTPS Let’s Encrypt
The concept of Traefik and K3s is wide. If you want to dive deeper, you can use Traefik Dashboards on your K3s clusters.
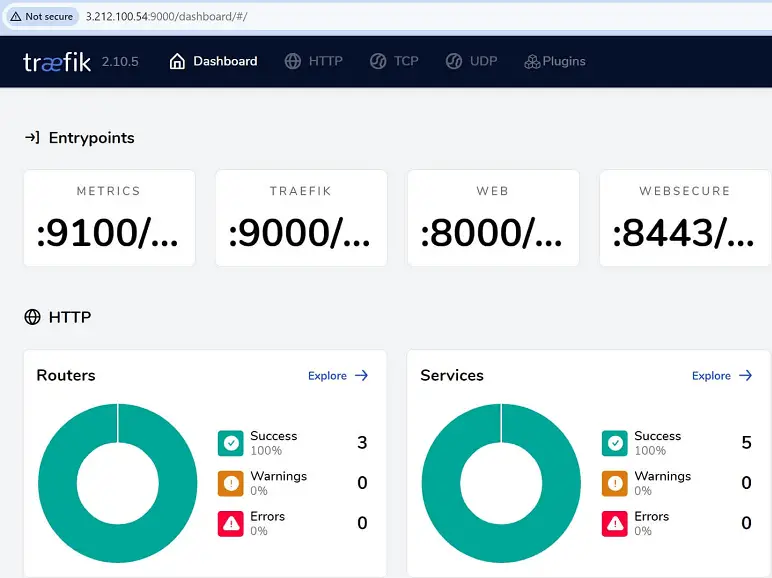
Any Traefik Ingress Controller can be accessed using HTTPS and Let’s Encrypt.
To understand these concepts further, check this comprehensive K3s and Ubuntu Server setup.
Conclusion
This helped you learn K3s with the Traefik Ingress Controller. I hope you can now use the Traefik Ingress Controller Example and Configure it with K3s.